AEGIS: A Single-Chip Secure Processor
G. Edward Suh, Charles W. O'Donnell, Dwaine Clarke, Marten van Dijk & Srinivas Devadas
What
We propose to design and build a single-chip secure processor, named AEGIS, that provides secure execution environments even under untrusted operating systems and physical attacks.
Why
It is becoming common to use a multitude of computing devices that are highly interconnected to access public as well as private or sensitive data. On the one hand, users desire open systems for ease-of-use and interoperability, but on the other hand, they require privacy mechanisms that restrict access to sensitive data, and authentication mechanisms that ensure data integrity. With the proliferation and increasing usage of embedded, portable and wearable devices, in addition to protecting against attacks from malignant software, we also have to be concerned with physical attacks that corrupt data, discover private data or violate copy-protection, as well as combinations of physical and software attacks.
Given these trends, computing systems have to achieve several goals in order to be secure. Systems should provide tamper-evident environments where software processes can run in an authenticated environment, such that any physical tampering or software tampering by an adversary is guaranteed to be detected. In private and authenticated tamper-resistant environments, an additional requirement is that an adversary should be unable to obtain any information about software and data within the environment by tampering with, or otherwise observing, system operation (We may refer to these environments as private tamper-resistant environments for brevity). Ideally, a computing platform should provide a multiplicity of private and authenticated environments wherein each process (or each user) is protected from all other users and potential adversaries.
How
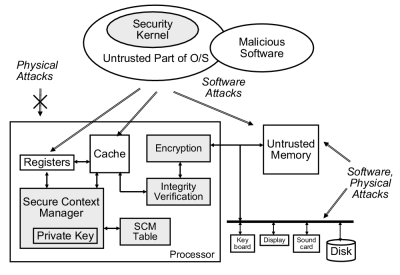
We build a secure computing system around a trusted processor with untrusted external memory and peripherals. Figure 1 illustrates this model. The processor is assumed to be trusted and protected from physical attack, so that its internal state cannot be tampered with or observed directly by physical means. The processor can contain secret information that identifies it and allows it to communicate securely with the outside world. This information could be the secret part of a public key pair protected by a tamper-sensing environment [3], or a Physical Random Function [1].
Figure 1: Our secure computing model.
On the other hand, external memory and peripherals are assumed to be untrusted. They may be observed and tampered with at will by an adversary. Therefore, the processor needs to ensure the integrity and the privacy of off-chip memory. We use two hardware mechanisms for this purpose.
- Memory Integrity Verification: A processor checks if the off-chip memory behaves correctly. Memory behavior is valid if the value the processor loads from a particular address is the most recent value that it stored to that address. If the contents of the off-chipmemory have been altered by an adversary, the processor should be able to detect, with high probability.
- Memory Encryption: To protect privacy, a processor needs to encrypt whenever data is stored in the off-chip memory. The major concern of encrypting off-chip memory access is its impact on the memory latency.
In our case when an owner of a computing system can be a potential attacker, the operating system (OS) cannot be completely trusted. Software attacks by the operating system or from other malicious software are therefore possible. To protect a system against untrusted operating systems, we use either a security kernel that operates with higher privilege than a regular OS or a hardware secure context manager that verifies the core functions of the OS.
Progress
The high-level specification of the AEGIS processor architecture has been outlined in our ICS paper [5], which provides secure execution modes even with an untrusted operating system and untrusted external memory. This architecture implements the tamper-evident and tamper-resistant environments.
We have developed two memory integrity verification mechanisms [2, 4]. In one case, we use hash trees to verify the integrity on every off-chip memory access. In the other case, we use multi-set hashes and verify a sequence of memory accesses. The overhead of our mechanisms is quite low.
For off-chipmemory privacy, we have developedan efficient encryption mechanism basedon one-time-pad scheme [4]. This new mechanism decouples the computations of conventional encryption algorithms such as AES from the memory accesses. This successfully hides a significant portion of encryption/decryption latency.
These new integrity verification and encryption mechanisms enable the implementation of a secure computingsystem withthe only trusted component being a single-chip AEGIS processor.
We have developed an FPGA prototype of the AEGIS processor based on the OpenRISC 1200 core [6]. This implementation uses physical random functions to reliably hold secrets instead of public key pairs, and currently accommodates single embedded applications.
Future
In the future we will extend our prototype to support a security kernel and multitasking. Eventually, we plan to build a custom silicon single-chip processor, and investigate issues with building secure embedded systems using the AEGIS processor.
We are also studying a few new architectural mechanisms. Currently, private data in off-chip memory are protected only by encryption. However, memory access patterns can leak private information as well. We are developing a hardware mechanism with low overhead to obfuscate memory access patterns.
Research Support
This work was funded by Acer Inc., Delta Electronics Inc., HP Corp., NTT Inc., Nokia Research Center, and Philips Research under the MIT Project Oxygen partnership.
References:
[1] Blaise Gassend, Dwaine Clarke, Marten van Dijk, and Srinivas Devadas. Silicon Physical Random Functions . In Proceedings of the Computer and Communication Security Conference, November 2002.
[2] Blaise Gassend, G. Edward Suh, Dwaine Clarke, Marten van Dijk, and Srinivas Devadas. Caches and Merkle Trees for Efficient Memory Integrity Verification. In Proceedings of Ninth International Symposium on High Performance Computer Architecture, February 2003.
[3] S. W. Smith and S. H. Weingart. Building a High-Performance, Programmable Secure Coprocessor. In Computer Networks (Special Issue on Computer Network Security), volume 31, pages 831860, April 1999.
[4] G. E. Suh, D. Clarke, B. Gassend, M. van Dijk, and S. Devadas. Efficient Memory Integrity Verification and Encryption for Secure Processors. In Proceedings of the 36th Int'l Symposium on Microarchitecture, pages 339350, Dec 2003.
[5] G. Edward Suh, Dwaine Clarke, Blaise Gassend, Marten van Dijk, and Srinivas Devadas. AEGIS: Architecture for Tamper-Evident and Tamper-Resistant Processing. In Proceedings of the 17 th Int'l Conference on Supercomputing (MIT-CSG-Memo-474 is an updated version), June 2003.
[6] G. Edward Suh, Charles W. O'Donnell, Ishan Sachdev, and Srinivas Devadas. Design and Implementation of the AEGIS Single-Chip Secure Processor Using Physical Random Functions. In Proceedings of the 32nd Annual Int'l Symposium on Computer Architecture, June 2005
The Stata Center, Building 32 - 32 Vassar Street - Cambridge, MA 02139 - USA tel:+1-617-253-0073 - publications@csail.mit.edu (Note: On July 1, 2003, the AI Lab and LCS merged to form CSAIL.) |