
| Technical Reports | Work Products | Research Abstracts | Historical Collections |
![]()

|
Research
Abstracts - 2006
|
Web Wallet: Preventing Phishing Attacks by Revealing User IntentionsMin Wu & Robert C. MillerIntroductionPhishing has become a significant threat to Internet users. Phishing attacks typically use legitimate-looking but fake emails and websites to deceive users into disclosing private information to the attacker. Most phishing attacks trick users into submitting their personal information online using a web form at a spoofed website. Even though using a web form to submit sensitive information is a common practice used by most legitimate sites, web forms have several problems that make phishing attacks effective and hard to prevent. First, the appearance of a web site and its web forms are easy to spoof. A web site can control what it looks like in a user's browser, so a site's appearance cannot reliably reflect the site's true identity. But users tend to decide site identity based on appearance. As a result, users may be tricked into submitting data to fraudulent sites. Second, web forms are used for submitting insensitive data as well as sensitive data. That is, the same kind of web form used to submit search keywords in one site is used to submit credit card information in another site. The semantic meaning of the input data is opaque to the browser. The browser fails to give different protections according to the sensitivity of the input data. Many proposed solutions to phishing use toolbars that show different types of security messages to help users to detect phishing sites. Users are also advised to look at the existing browser security indicators, e.g., the URL displayed in the address bar and the lock icon displayed in the status bar when a connection is SSL-protected, to detect phishing sites. However, controlled user studies [2] have shown that these security indicators are ineffective against high-quality phishing attacks. ApproachWe have designed new software, called the Web Wallet (figure 1), to prevent phishing attacks [1]. The Web Wallet is based on the following two design principles:
When a user sees a web form requesting sensitive information, she presses a dedicated security key on the keyboard to open the Web Wallet. Using the Web Wallet, she may type her information or retrieve her stored information. The information is then filled into the web form. Before the fill-in, the Web Wallet always checks if the current site is good enough to receive the sensitive information. If not, the Web Wallet requires the user to explicitly indicate where she wants the data to go by showing her a list of sites, including the current site, and lets her choose the site that she wants to submit the data to. If the user's intended site is not the current site (which probably indicates phishing), the Web Wallet shows a warning to the user about this discrepancy, and gives her a safe path to her intended site. To correctly use the Web Wallet, users only need to remember one simple rule: “Always use the Web Wallet to submit sensitive information by pressing the security key first.” The hidden negative statement of the same rule is that “never submit sensitive information directly through the web form because it is not a secure practice.”
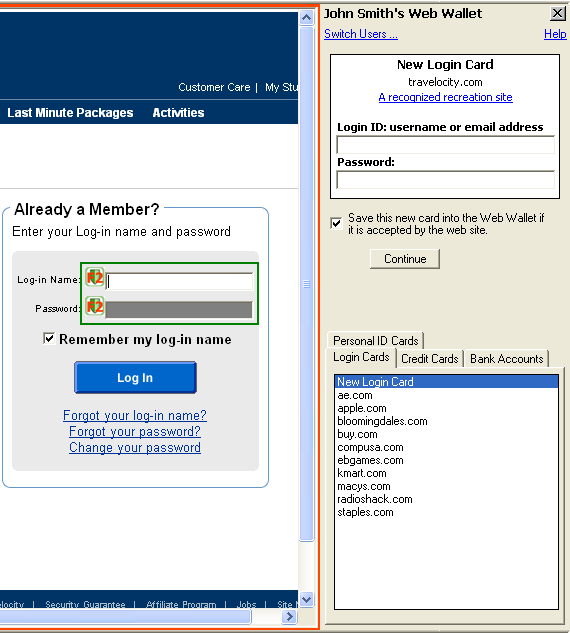 Figure 1: The Web Wallet interface User StudyWe have run a user study to test the Web Wallet interface. Each subject was told to act as the personal assistant of John Smith. John Smith forwarded 20 emails to her in random order and asked her to go to 20 different web sites, log in with his password, and add items to his wish list. Five of the 20 forwarded emails were attacks, with links directing the subject to simulated phishing web sites. Phishing attacks were simulated by connecting to the real web site but changing the address bar to display a different hostname (indicating that the web page was from an unusual source). The results are promising:
But there are also negative results which we plan to deal with in future research:
Future WorkWe see many ways to improve the design of the Web Wallet. For example, the Web Wallet should not only support login using an existing password, but also other password-related activities, such as registering a new account and changing the password of an existing account. The Web Wallet should also protect other types of the sensitive data. The full-featured Web Wallet should by default protect credit card information, bank account information and personal identity information as well. Eventually, the Web Wallet should be able to protect any personal data defined by P3P. Clear and detailed explanations should be added to the Web Wallet interface in order to help users better understand the purpose of the Web Wallet and to correctly use it, i.e., open it whenever necessary. We also have to find a solution to prevent the Web Wallet itself from being spoofed. We plan to use image recognition techniques to detect the presence of a fake Web Wallet. References:[1] Min Wu, Robert C. Miller, Greg Little. Web Wallet: Preventing Phishing Attacks by Revealing User Intentions. Submitted to Symposium on Usable Privacy and Security 2006. [2] Min Wu, Robert C. Miller, Simson L. Garfinkel. Do Security Toolbars Actually Prevent Phishing Attacks? Conference on Human Factors in Computing Systems 2006.. |
||||
|