
| Research Abstracts Home | CSAIL Digital Archive | Research Activities | CSAIL Home |
![]()

|
Research
Abstracts - 2007
|
Collaborative Intrusion Detection Using Network KnowledgeJi Li & Karen SollinsIntroductionIntrusion detection in large-scale networks requires a new approach to monitor and respond to security incidents. Host-based collaborative intrusion detection has been a promising direction. A key challenge in a collaborative intrusion detection system is that alerts from end hosts need to be propagated efficiently and quickly among participants so that an intrusion decision can be made before the worm infect most of the hosts. Many current mechanisms use simple gossiping protocols or peer-to-peer protocols [1,2,3]. We believe a good cooperative messaging protocol can be made more efficient by taking advantage of the knowledge from the network. In this work, we propose a region-based message propagation protocol. We implement our mechanism on the DETER testbed [4] and compare it with a popular gossiping protocol. By doing this case study, I want to demonstrate that there can be both accuracy and efficiency improvements for intrusion detection to take advantage of the knowledge plane. Our ApproachA gossiping protocol was proposed for shareing the results of weak local detection in [3]. Its decision making is completely distributed in that hosts exchange information using an epidemic spreading protocol without any organizing structure or consideration of network topology. When a potential intrusion is detected by an end host, it forwards the alert to m randomly selected neighbors, and then its neighbors forward the alert to each of their m neighbors, together with their own observations (alert or not), and this continues. Each host computes the possibility of intrusion using all the alerts it has received. If a host determines that there is an intrusion, it broadcasts the decision to all hosts. We propose to organize hosts into regions using the knowledge from the NetKP. Hosts are clustered into regions based on their distance. Within each region, hosts elect a leader using distributed leader election algorithm periodically. Leaders of different regions form a complete graph if the number of leaders is small or other organizations such as multiple disjoint trees [7]. When hosts detect potential intrusion attempts, alerts are sent to its local leader directly. The local leader aggregates alerts from local hosts, and then exchanges this information with leaders of other regions. Therefore, each leader has an approximate global view of the intrusion situation. Whenever a leader has enough information to make a decision, it announces its decision to both its local hosts and all the other leaders. Leaders may or may not need to reach an agreement on the decision, depending on their policy and administration. Our mechanism is similar to [2] in the hierarchy of local detectors and leaders (global detectors in [2]). The difference is that in [2], each local detector sends its decision to a randomly selected subset of a large set of global detectors. The local detectors have to maintain the information of all or most global detectors, and the communication does not consider any network-layer information. ExperimentsI ran experiments on 42 nodes on DETER. The experiment topology was similar to a dumbbell. Intrusion was emulated using WormSim [6]. Intrusion was detected when a non-vulnerable host received an access attempt on an unserved port. Our approach and a gossiping protocol are compared. Both methods use distributed sequential hypothesis testing to detect global intrusion. Sequential hypothesis testing was first adopted to intrusion detection by Jung et al. in [5]. I compared two aspects: detection speed and cost. Detection speed measures how fast hosts can reach a decision on intrusion detection. Detection cost consists of two metrics: (1) the number of messages that hosts propagate to reach a decision; (2) the number of infected nodes by the time of decision. The initial results show our approach can increase the detection speed and reduce the traffic. The following figure shows the initial performance. 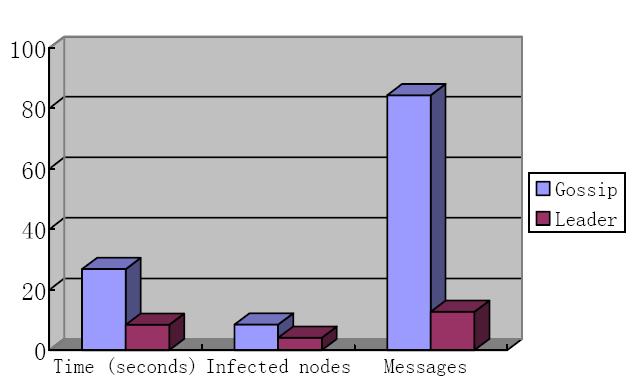
Future WorkThe experimental results suggest that the network knowledge plane can improve intrusion detection by providing valuable network-layer knowledge to intrusion detection systems. In the near future I will follow up with a series of further experiments. (1) Allow the gossip protocol to run locally within a cluster. This will allow us to improve our understanding of the tradeoff between network costs and both speed and correctness of detection. (2) Move to the model in which local and global detection are distinct. We plan to study two different questions here. One is that each local detector can be specialized. The other is that a cluster of global detectors might be specialized by region or enterprise, allowing for improved scaling. (3) Create a security policy that prohibits the exposure of most local information, but allows for the report of definitive attacks. This is an example of understanding and utilizing incentives effectively. (4) Enhance the reporting scheme to reflect a signature of a worm, if detection has occurred. We expect this to significantly reduce the impact of false positive reports, and enable the disentanglement of simultaneous worm attacks. References[1] D. J. Malan and M. D. Smith. Host-based detection of worms through peer-to-peer cooperation. In Proceedings of The ACM workshop on rapid malcode (WORM'05), New York, USA, 2005. [2] D. Dash, B. Kveton, J. M. Agosta, E. Schooler, J. Chandrashekar, A. Bachrach, and A. Newman. When gossip is good: Distributed probabilistic inference for detection of slow network intrusions. In Proceedings of the 21st National Conference on Artificial Intelligence, 2006. [3] S. G. Cheetancheri, J. M. Agosta, D. H. Dash, K. N. Levitt, J. Rowe, and E. M. Schooler. A distributed host-based worm detection system. In Proceedings of the 2006 SIGCOMM workshop on Large-scale attack defense (LSAD'06). New York, NY, USA, 2006. [7] The DETER Testbed. http://www.isi.edu/deter/. [5] J. Jung, V. Paxson, A. W. Berger, and H. Balakrishnan. Fast Portscan Detection Using Sequential Hypothesis Testing. In IEEE Symposium on Security and Privacy, Oakland, CA, May 2004. [6] J. McAlerney. An internet worm propagation data model. Master's thesis, University of California, Davis, CA, September 2004. [7] J. Li, K. Sollins, and D.-Y. Lim. Implementing aggregation and broadcast over distributed hash tables. In ACM SIGCOMM Computer Communication Review, Volume 35, Number 1, January 2005. |
||||
|