
| Research Abstracts Home | CSAIL Digital Archive | Research Activities | CSAIL Home |
![]()

|
Research
Abstracts - 2007
|
MUPPET: Mobile Ubiquitous Privacy Protection for Electronic TransactionsWinnie Cheng, Jun Li, Keith Moore & Alan H. KarpIntroductionMobile devices are becoming increasingly capable and connected. Mobile technologies have grown to deliver more computing power and features than desktop PCs of the last decade. Today, smartphones and PDAs can run complex operating systems and standalone databases. They often include a wide range of communication options from Bluetooth to GPS. With these advances, integrated services that were once impractical are turning into reality. Not only can users send e-mail and surf the web with these gadgets, they will soon be serving as a user's wallet and much more. Currently, little attention has been placed on the privacy ramifications of next generation mobile service infrastructures. A user's mobile device can potentially contain very sensitive information revealing the owner's identity, payment information and various usage histories. At the same time, service providers are leveraging the interconnectivity of information sources and advances in information retrieval to provide intelligent services that target the particular user. Automatic customization and personalization of content delivery bring relevant information to users when they want it and where they want it. As these mobile companions interact with various service providers in the environment, information may be given out unintentionally. Existing mobile privacy protection mechanisms ([1],[2]) often rely on pre-established trust relationships or focus on policy specifications defining contracts on how data should be handled under different circumstances and the obligations of service providers to ensure proper handling of this data. Enforcement is left to the legal system. Legal consequences may deter some malicious uses of sensitive collected data. However, there are many grey areas in defining and justifying proper uses of collected data. Today, users have little dynamic control over the dissemination of their information. Mobile environments pose additional challenges in protecting privacy. A mobile digital companion may interact in many ad-hoc networks with different service access points as the user roams around. This makes a priori trust relationships difficult to establish and manage. Imagine Alice the shopper who carries her smartphone around the shopping mall of the future. Her smartphone is her electronic wallet and contains her preferences and transaction history. As Alice walks through various stores in the shopping mall, advertisement displays and information kiosks communicate with her mobile device to find the most relevant products and offers for Alice. While the interaction between Alice's smartphone and these kiosks can enrich her shopping experience, these new mobile service infrastructures raise a number of privacy concerns. The underlying communication should be transparent to a user like Alice. At the same time, Alice should have greater control over the information that is exchanged. ApproachWe have developed MUPPET to address these issues. MUPPET is intended to serve as a trusted privacy protection system running on the user's mobile device. Our system focuses on restricting the disclosure of sensitive information at the source. MUPPET assumes that all user data to be protected is stored locally on a device such as a smartphone or PDA. This device participates in the exchange of information involving user data with other service providers. MUPPET assumes that service providers ask questions in the form of database queries to the user. These questions can potentially involve the release of sensitive data. In most cases, users are interested in replying to the service provider for some benefits or rewards. MUPPET incorporates a number of novel techniques to give users control over the release of their data. First, it introduces Operation-focused Access Control, a purpose-based access control model that supports flexible and fine-grained policies using operation labels. Second, our system allows Reward-Driven Information Exchange. It provides a protocol for explicit communication of justifications and rewards and tunable privacy policies based on ongoing evaluation of the information exchange. Third, MUPPET includes a Purpose Detection Engine that supports explicit as well as implicit purpose activations based on context or authorizations. 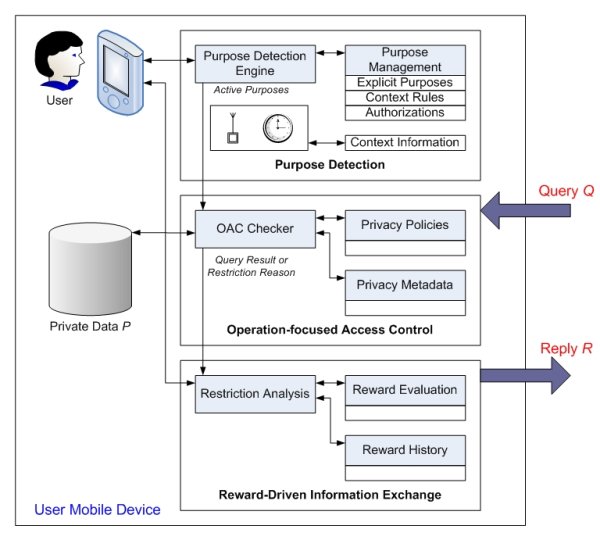
The approach our system takes is most closely related to work on purpose-based access control in database systems ([3], [4]). A purpose can be labeled with a relation, attribute, sets of attributes or tuples to define when the data object should be revealed. In these systems, a service provider that has been certified by a trusted third party to fulfill a particular purpose may retrieve data objects that have been labeled for that purpose. This method has the advantages that policy specification is very natural and access enforcement is lightweight. Hence, it is attractive for our mobile service environment. However, current systems provide a binary decision on the access of a data object. That is, either the access is allowed and data is revealed in its original form or access is denied. Often, a user may be willing to reveal some related information or fuzzified form of the data object. For example, as mentioned earlier, Alice the shopper may be willing to reveal her age group (that is, +/- 5 years of her age) but not her exact age. This information is still valuable to a service provider that attempts to retrieve advertisements aimed at different groups. MUPPET introduces Operation-focused Access Control (OAC) to allow typed data objects that can be subject to different operations such as transformations and perturbations before disclosure. The OAC checker is conservative in enforcing policies. Users are likely to be, and are encouraged to be, more stringent on the policy specification initially when little is known about the service provider and its environment. When a query is denied, MUPPET provides an alternative protocol to allow the service provider to justify its reason for the data collection and to entice the user with rewards. MUPPET presents the user with the reason and reward to be supplied by the service provider along with an analysis of the privacy concerns on the requested query. The user can examine all the evidence to make an informed decision as to whether to grant temporary access. MUPPET logs the decision and allows the user to evaluate the level of satisfaction from the usefulness of the information exchange and the promised reward. The Purpose Detection engine should determine the set of active purposes that match closely with the user's intent. A reliable mechanism to specify this intent is to ask the user to communicate with MUPPET explicitly via a graphical user interface. MUPPET also provides various implicit mechanisms. Context-aware rules can be defined to activate purposes depending on location, time and other sensor inputs. Authorization-based techniques allow purpose to be granted like a capability to a service provider. ProgressWe have implemented a version of MUPPET targeted for Pocket PCs. We have tested it on various versions of HP iPAQs including the HW6515A model running Microsoft Windows Mobile 2003. The prototype uses the embedded database SQL Server CE to store user data as well as the policies and metadata used in MUPPET. To validate our design, the MUPPET prototype has been integrated with a coupon personalization application for two different service providers in an experimental retail kiosk setting. Research FundingThis work is funded by Hewlett-Packard Laboratories. References:[1] M. Langheinrich. A privacy awareness system for ubiquitous computing environments. In Proceedings of the 4th international conference on Ubiquitous Computing, pp. 237--245, London, UK, 2002. [2]J. I.-A. Hong. An architecture for privacy-sensitive ubiquitous computing. PhD Thesis, University of California at Berkeley, Computer Science Division, 2005. [3] R. Agrawal, J. Kiernan, R. Srikant, and Y. Xu. Hippocratic databases. In Proceedings of the 28th International Conference on Very Large Databases, Hong Kong, China, August 2002. [4] J.-W. Byun, E. Bertino, and N. Li. Purpose based access control of complex data for privacy protection. In SACMAT, 2005, pp. 102–110. |
||||
|