UIP: A Zero-Configuration Architecture for Ad Hoc Internet Naming and Secure Global Connectivity
Bryan Ford, Chris Lesniewski-Laas, Jacob Strauss & Frans Kaashoek
Introduction
The vision of "ubiquitous network computing"---% enabling networked computers to interact seamlessly wherever they are located---% is actually becoming more remote as the Internet evolves. The instability of DHCP-assigned IP addresses, the prevalence of network address translation (NAT), the security vulnerabilities in common end-user machines, and the costs and technical skills required to register and activate global domain names all contribute to this unfortunate trend.
UIP is a practical and evolutionary extension to the Internet architecture that offers a coherent solution to these problems. UIP combines a new identity-based routing layer with novel DNS extensions for ad hoc naming. Identity-based routing provides hosts with stable, globally unique, self-configured identities, and enables hosts to remain connected via secure channels even when behind multiple levels of NAT or while roaming between networks. UIP's naming extensions make end hosts act as peer-to-peer name servers, enabling technically unskilled users to "bookmark" and freely exchange secure name-to-identity bindings. Through these backward-compatible extensions, UIP provides the global naming and connectivity features essential to ubiquitous network computing, in a security model based not on traditional hierarchical administrative structures but on the ad hoc "web of trust" inherent in the relationships among ordinary people. A prototype implementation of UIP demonstrates the feasibility and usefulness of this concept without incurring a substantial performance impact.
Architecture
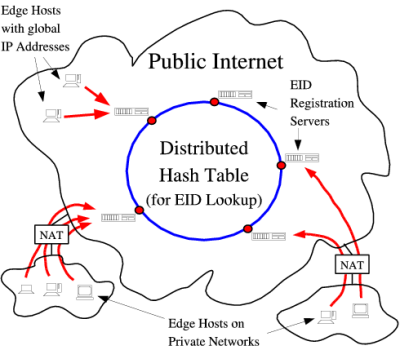
To enable hosts to be globally accessible even from behind NATs or while roaming from one IP address domain to another, UIP provides hosts with cryptographic endpoint identifiers (EIDs) derived from the host's public key. Transport- and application-level protocols refer to hosts via location-independent EIDs instead of location-specific IP addresses, enabling seamless host mobility without breaking transport connections across IP address changes. UIP introduces a secondary routing layer above IP that can traverse different IP address domains automatically, even when communicating hosts are behind multiple NATs. UIP also provides ad hoc EID-based connectivity between hosts on link-layer networks where TCP/IP networking is not operational at all, such as when there is no DHCP server or there are IP address conflicts. By default, UIP implements automatic IPSEC-style encryption and authentication for all application-level traffic, without the traditional inconvenience and administrative costs of public key infrastructure or manually-configured secrets.
When a UIP host is connected to the global Internet and has a valid IP address, in our current design, it contacts and registers its own EID with one or more registration servers, which are well-connected nodes on the Internet with globally routable IP addresses. Registration servers cooperate with each other by exchanging location information about the EIDs they have registered, allowing any host to locate and connect with any other by its EID.
The problem of distributing EID-to-location mapping information and processing load across many registration servers is solvable using a distributed hash table (DHT). We envision a global `ring' of well-known registration servers analogous to the top-level domain name servers, though perhaps more numerous. To ensure that registration servers implement the DHT protocol properly and share the collective resources of the DHT fairly, this ring would not be open to all, but only to hosts whose owners have made a contractual commitment to run their registration servers according to established rules.
Implementation
We have built a prototype implementation of UIP that demonstrates the most important features of the architecture, such as identity-based routing across the Internet and ad hoc link-layer networks, automatic NAT traversal, and application-transparent communication security. Our prototype consists of uipd, a daemon that runs on each edge host and implements identity-based routing and communications security for that edge node; a simple registration server, which maps EIDs to the (IPv4 address, port) pair where the correct uipd currently resides and mediates NAT traversal; and a stub library through which applications invoke UIP services.
Acknowledgements
This research was conducted as part of the IRIS project, supported by the National Science Foundation under Cooperative Agreement No. ANI-0225660.
References:
[1] Bryan Ford. Unmanaged Internet Protocol: Taming the Edge Network Management Crisis. Second Workshop on Hot Topics in Networks, Cambridge, MA, November 2003.
The Stata Center, Building 32 - 32 Vassar Street - Cambridge, MA 02139 - USA tel:+1-617-253-0073 - publications@csail.mit.edu (Note: On July 1, 2003, the AI Lab and LCS merged to form CSAIL.) |
